This post is not a tutorial, just some thoughts on the topic. There are plenty of tutorials out there that talk about protecting your RESTful Node/Express based APIs using some form of token-based authentication. Some of them are pretty straightforward to follow, some not. But most of them have one thing in common — delegating the authentication part to Passport.js. While that’s not a bad idea, using Passport.js for anything other than basic HTTP authentication can be bewildering, especially when you want to implement a more secure auth such as OAuth or HTTP Bearer.
HTTP Basic Authentication is a big NO-NO
Never, ever think of doing this just for the sake of making it easy to call your APIs from client-side code. Basic authentication is insecure. Period. It’s way too easy to crack.
Start with a simple JWT-based Token Authentication
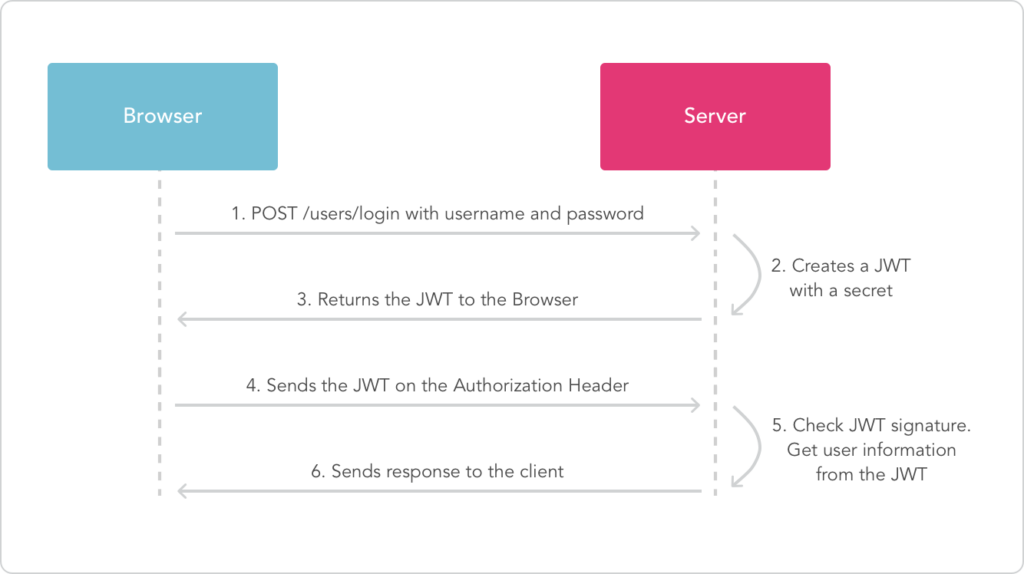
JWT has pretty much become the standard auth token format. It’s used by small to large enterprises alike. Before actually taking the dive, it will immensely help to understand the anatomy of JWT. Once you’ve done that, give this tutorial a read. It’s one of the best and easy to follow tutorials I’ve come across on this topic.
TL;DR — JWT is a self-contained piece of information. It makes session-based auth a thing of the past. No more creating database tables to store user sessions and no more writing server-side logic to handle them. jsonwebtoken npm package makes it easy to integrate a JWT-based auth flow in a Node/Express based application. Most of the magic happens in your API router’s middleware, which acts as the single place to authenticate ALL your APIs.
Use bcrypt for storing hashed passwords
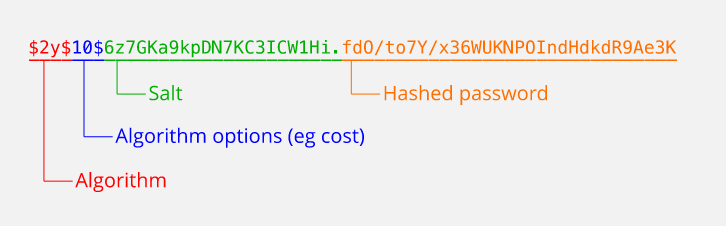
If you’ve gotten this far in this post, I’m sure you know to NEVER STORE PASSWORDS IN PLAIN TEXT. People have amazing theories. Some n00bs make the mistake of storing plain text passwords, thinking that modern database systems are themselves secure enough and unhackable. They are totally wrong. Yes, database vendors like Oracle and Microsoft do their best to make their systems highly secure and robust but what good is that security when the app itself is stupidly vulnerable?
Developers who realize this bit actually store passwords as irreversible hashes, sometimes relying on good ol’ MD5 or SHA-1 algorithms. But even these aren’t secure enough. There are better and more secure hashing algorithms, such as bcrypt. I’ve found the bcrypt-nodejs npm package to be pretty straightforward.